Hacking a Massive Steam Scamming and Phishing Operation for Fun and Profit
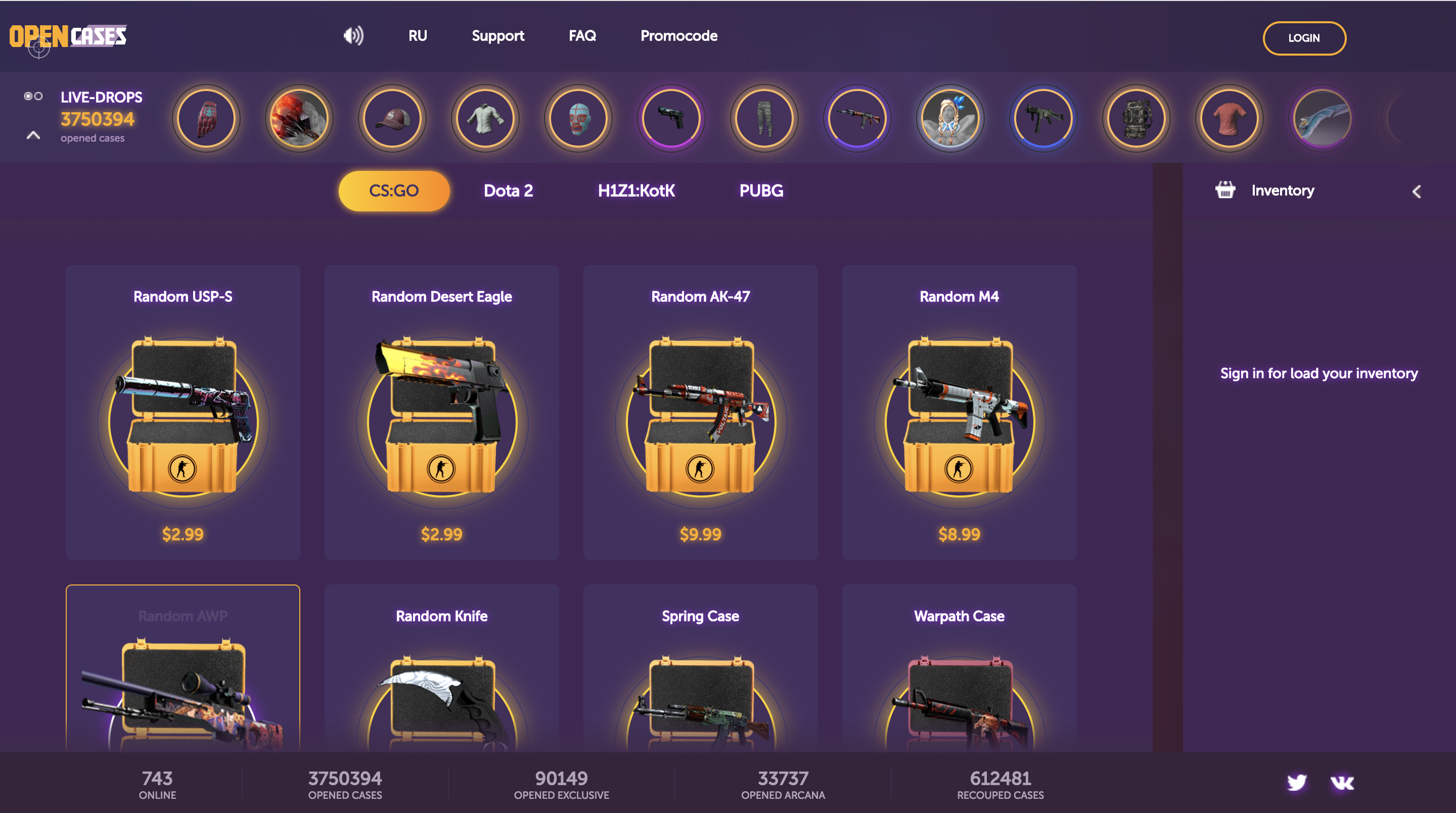
When I'm not doing bug bounty or studying for school I'll often be playing Counter-Strike: Global Offensive or PLAYERUNKNOWN'S BATTLEGROUNDS. Both of these games are awesome and really fun to play, but something interesting about them is that their tradable in-game items are very valuable.
Due to the high prices of items and often underage inexperienced players, these communities are ripe for scamming and fraud.
One day, after accepting an unknown friend request, my account became spammed with additional friend requests. All of the accounts had titles like "CSGO money" or "CSGO gambling". They would send periodic messages that all followed a very similar format...

Every one of the messages I received would have (1) a link to a gambling or trading website, then (2) some sort of promotional incentive.
At first I thought this was just a cute way to advertise gambling websites, but it wasn't until someone had began messaging me accusing me of taking over their account that I got suspicious the websites were mischievous or fraudulent.
dyoungclaus: Why do I have you added? dyoungclaus: Can you please explain why you hacked my account? dyoungclaus: ???
The person who was messaging me had initially began our relationship by sending me a random friend request, followed it with an advertisement, then lastly accused me of hacking their account. My guess was that the link they were advertising was somehow tricking the user into giving account access to a third party or was phishing their credentials.
At this point I was curious what was actually being hosted on the website, so I took a look.

The first website I looked at (keep in mind I received at least 50 of these messages each with different domains) had an interesting premise...
- Deposit skins that would be translated into currency
- Use said currency to purchased a "case" which would give you a chance to get a more valuable item
- Cash out your winnings back to your account. Since all of this was controlled by an unknown third party (whoever owned the website) and not the actual game, there was very little trust on whether or not one could actually win the "rarer" items (anything that costs more than the case itself).
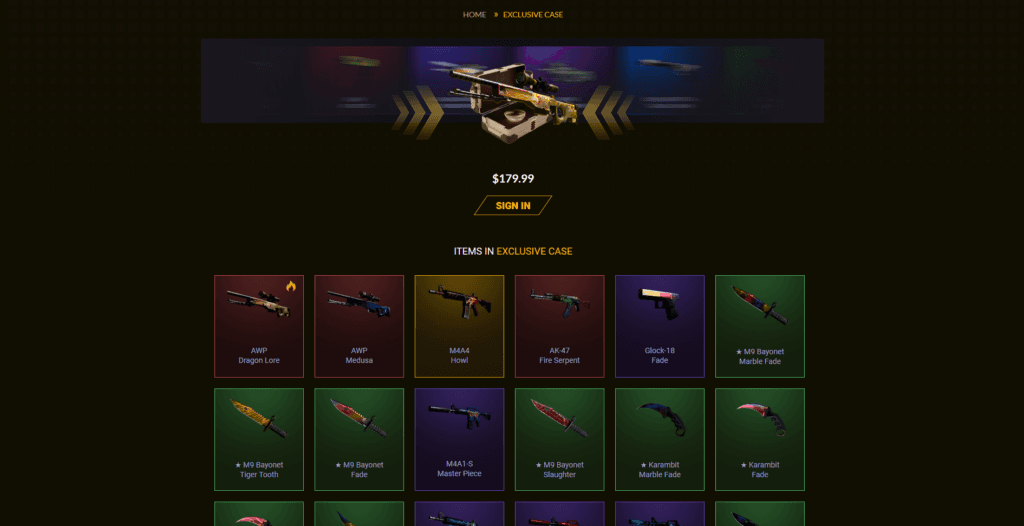
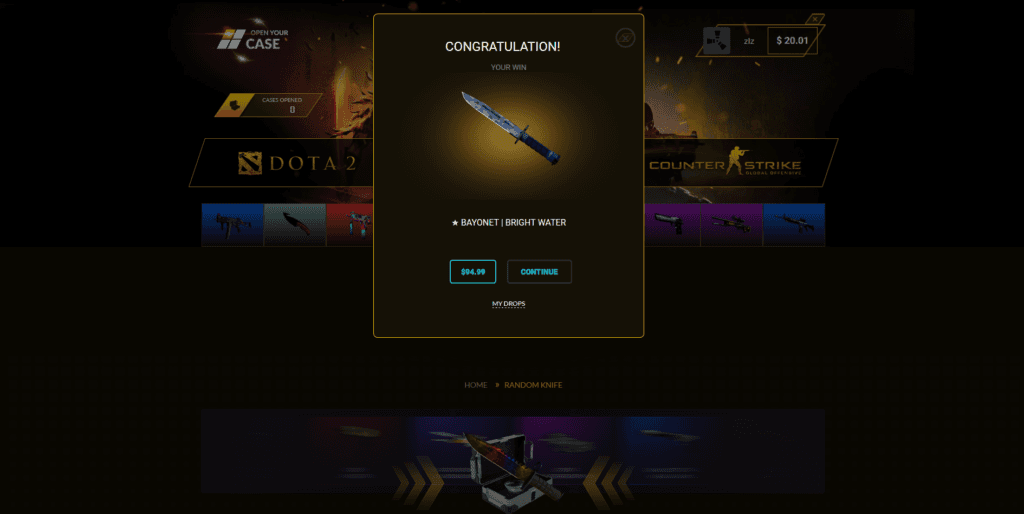
One of the questions I hadn't even thought about was "can you even withdraw your items?" - the answer was of course "no".

The scam was pretty easy to follow: tell users that they won an item after receiving a crazy promotion, ask them to deposit more than $20, don't give them their "winnings".
There were still a few things that confused me about this operation...
- How were they getting so many legitimate accounts to advertise with?
- There were at least 50 different domains I'd seen from private messages. Who were operating these websites?
- How much money were they making from scamming people?
Investigation
After opening two separate websites from two separate people I went ahead and identified that they were almost identical versions of each other...

At this point I realized that they all had to be tied together somehow, but I still wasn't really sure how these were being setup and distributed. One of the first things I decided to do was treat this like a normal bug bounty program and try to identify who was hosting the application and the information the server gave to us. I went ahead and opened Burp then sent a standard HTTP request to the website. The following is the response I received.
HTTP/1.1 200 OK
X-Powered-By: SomeSpecificString
X-RateLimit-Limit: 200
X-RateLimit-Remaining: 199
Access-Control-Allow-Origin: *
Access-Control-Allow-Headers: Origin, X-Requested-With, Content-Type, Accept
Content-Type: text/html; charset=utf-8
Content-Length: 53748
ETag: W/"d1f4-ZwMTxTE0SgpKtTCYdOrz9CjojXk"
set-cookie: cax9IuiMGwowstealmycookiemuch?7TY57q=s%3A0QWXsdonotstealmycookienoobQ5oDGAIoO.7K43b%2FKnVd%2Bq2gb0oT63nbtDG4; Path=/; HttpOnly
Date: Wed, 09 May 2018 00:51:18 GMT
Connection: close
If you've done any sort of bug bounty one of the things that you'll notice about the above HTTP response is that there is a very unique header returned...
X-Powered-By: SomeSpecificString
This puzzled me because this was the first time I'd seen this header... I did what anyone would do and Googled it.
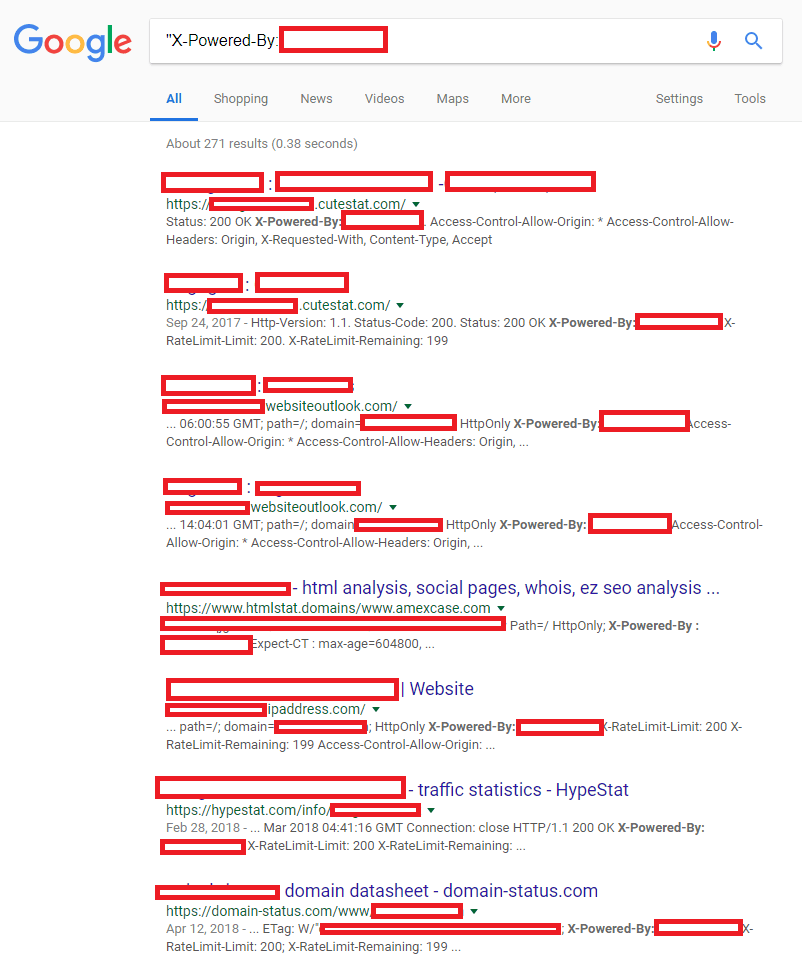
There were almost 300 results for the specific header that were all tied to CSGO gambling or trading websites. This wasn't a true count of how many of the websites existed as many were websites like "htmlstat.domains" or "ipaddress.com", but it was definitely interesting seeing how this one unique string tied them all together.
The next step I took was to go to Shodan and get a more specific idea of how many of these websites existed...
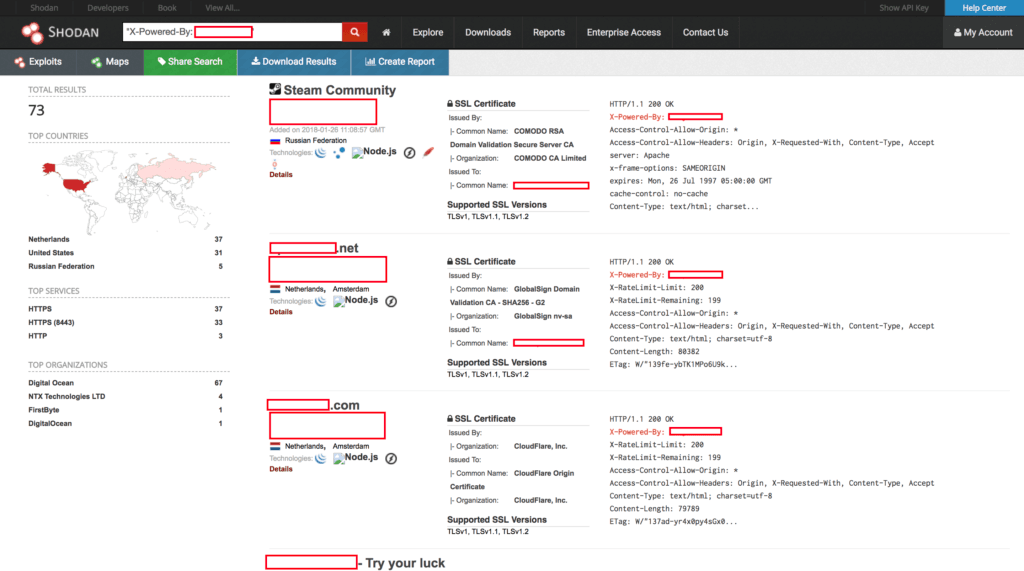
It appeared that Shodan had already fingerprinted 73 of these hosts, but many of them were not actually gambling websites. Below is an example of one that didn't follow the format described in screenshots above...
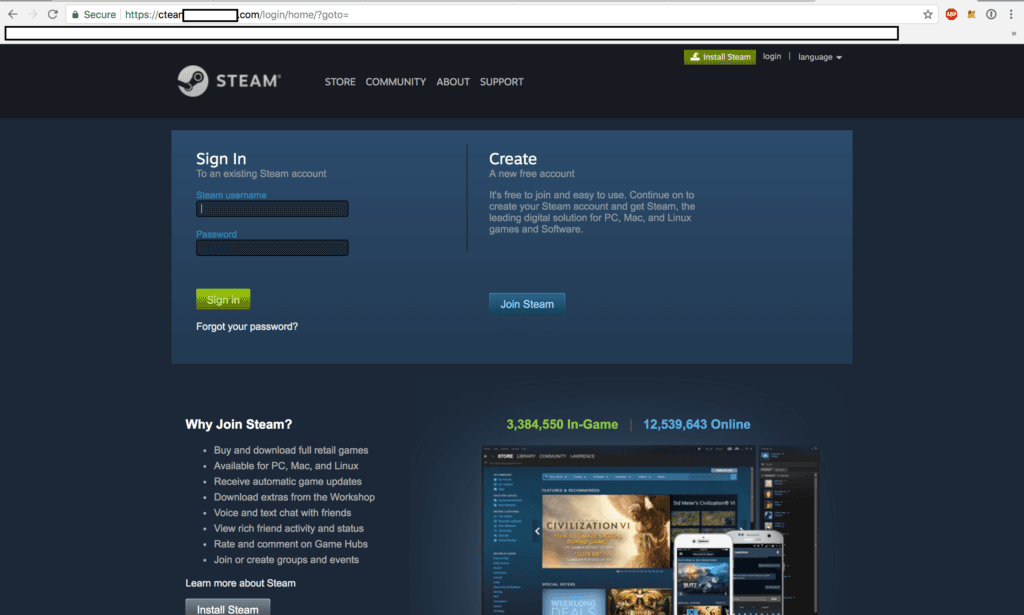
Notice anything peculiar about the above screenshot? If you didn't spot it, ctean***********.com is most definitely not steamcommunity.com. This was most likely how they were retrieving all of the accounts to spam with.
After dorking with the domain for a while and receiving nothing interesting, I decided to send a blind XSS payload and hop offline for a few hours in vain hopes that the website wasn't sanitizing HTML and would therefore allow me to execute arbitrary JS in the scammers instance which would allow me to see the panel that held credentials.
Hacking the Hackers
After waking up from my short nap I noticed the multiple fires that had executed using my favorite blind XSS tool XSS hunter.
<html lang="en"><head>
<meta charset="UTF-8">
<title>VGGSTEAM Admin Panel</title>
<script src="//cdn.jsdelivr.net/npm/alertifyjs@1.11.0/build/alertify.min.js"></script>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/font-awesome/4.7.0/css/font-awesome.min.css">
<link rel="stylesheet" href="//cdn.jsdelivr.net/npm/alertifyjs@1.11.0/build/css/alertify.min.css">
<link rel="stylesheet" href="//cdn.jsdelivr.net/npm/alertifyjs@1.11.0/build/css/themes/default.min.css">
<link rel="stylesheet" href="/assets/css/app.css">
<script src="/assets/js/socket.io-1.4.5.js"></script>
<script src="/assets/js/jquery.min.js"></script>
<script src="/assets/js/app.js"></script>
Just from observing the DOM I was able to determine that this was an administrator panel for whatever phishing or scamming service that they were running. What had happened was...
- I had provided my XSS hunter payload as a username for the phishing website
- The phishing website received my input then served it to the victims browser under a "failure" message since the credentials were not valid
- The XSS hunter payload sent me the browser DOM, cookies, victim IP address, and endpoint that it executed on

- A screenshot of the admin panel of the phishing website taken using XSS hunter. Attached are logs that demonstrated attempts to login to the phished accounts, then the associated 2FA code sent when the victim had it enabled.
The attached endpoint where the XSS payload fired was shown as ctean*******.com/admin/8vya1znto4wqoyjbkqr5q8au3xgsip08. The first thing I did was visit this endpoint and I was immediately logged in as an administrator.
The reason being for this (I assume) is that the attackers assumed that no-one would be able to predict or guess the location of 8vya1znto4wqoyjbkqr5q8au3xgsip08 and therefore did not feel that authentication was required to access the administration panel.
After browsing around for a while it was apparent that the compromised accounts were immediately searched for valuable inventory items, and if they existed, they would be traded to the attacker and emptied out. There were hundreds of compromised accounts listed on this domain alone. Below is an example of how the accounts were organized.
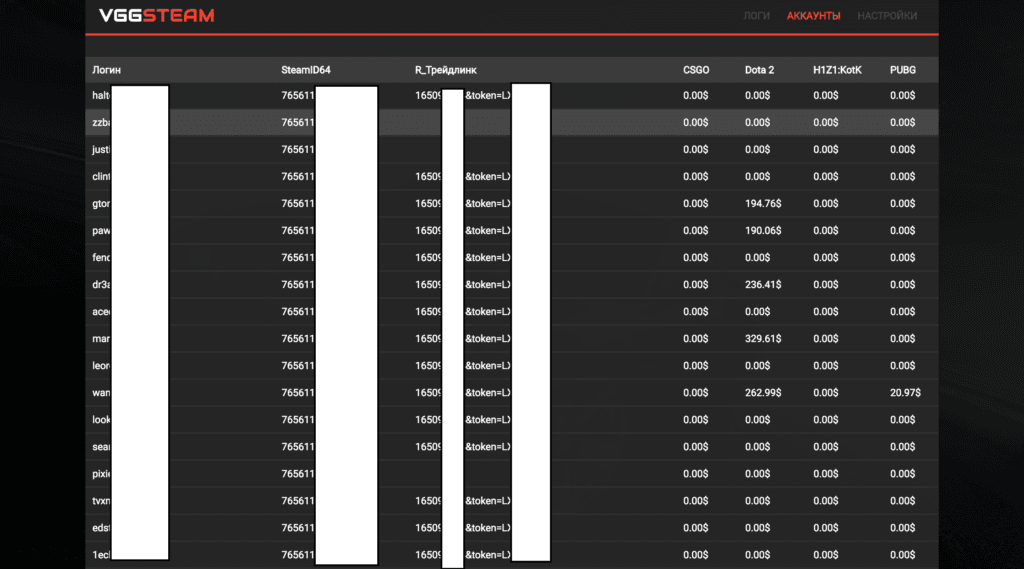
Interestingly enough, immediately trading from a new device didn't trigger Steams "new device, no trading" policy. The hackers had most likely found a bypass for this, which is even more interesting.
The website had additional interface for sending bulk messages on behalf of the users (this is probably how I got so much spam) and a button that would log me into the victims account without having to authenticate anywhere. It appeared the website had abused some functionality of Steam's sign in feature that allowed attackers to store sessions on a third party website and essentially create panels where they could click a button and fully access someones account.
At this point I had decided to report the massive operation to Valve's bug bounty program through the HackerOne platform as I had been invited as a private participant a few months ago.
Even though this wasn't a direct security vulnerability in Steam, I still felt as if reporting through the HackerOne platform was the best option as I would be able to aptly describe this issue and have a conversation regarding how I bulk identified these websites versus a spammy looking email to their support who most likely not understand what the report was addressing.
Timeline
- January 29th - report issue to the private Valve HackerOne program
- January 29th - receive response asking for a list of compromised accounts
- January 31st - issue triaged
- February 1st - $1,000 reward given for effort put into the report
Notes
This isn't something Valve normally pays for. The reason for receiving a bounty is as follows:
"Thanks for the report. While this report doesn't involve assets we have control over we have taken action on the effected user accounts so they suffer as little harm as possible. Normally a report on something we don't control would not be eligible for a bounty, but in this case the level of detail in the report warrants a payout."
I hope you enjoyed the write up! Feel free to follow me on Twitter or leave a comment with any questions or comments!
Huge shout out to @NahamSec for pushing me to figure out what was going on!